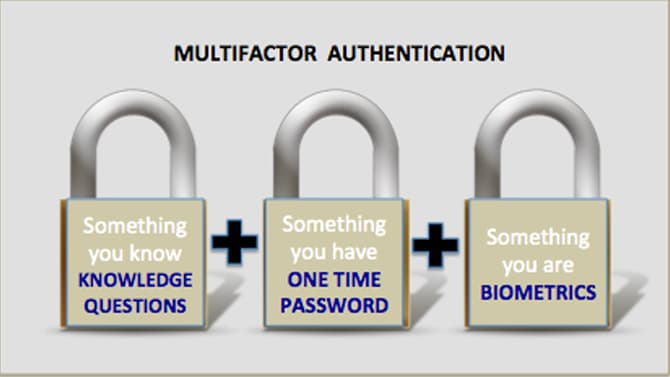
Nov 16, 2019 | 2FA, Best Practices, Business, Computers, credentials, Cyber breaches, cyberattacks, Cybersecurity, Employees, Employees, Hacking, Hacking, hardware token, Internet, Laptops, Malware, MFA, Phishing, Radio Show, Radio_Show, Security, Security, Technology
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...

Nov 9, 2019 | Applications, Artificial Intelligence, Audit Logs, Best Practices, Business, credentials, Cyber breaches, cyberattacks, Cybercrime, CyberTraining, data sharing, Data Storage, Databases, Employees, Employees, Firewalls, Firewalls, Hackers, Hacking, Hacking, Hacks, Hard Disks, Intellectual Property Theft, Laptops, Liability, Malware, Malware, Networking, Networking, Patching, Radio Show, Radio_Show, Ransomware, Routers, Security, Security, Security Alerts, segmentation, Software As A Service, Switches, Technology, Updates
Cyberbreaches cause Small Businesses to Close Cybercriminals have found a lucrative new target – the small business. Unfortunately, for a tenth of them the breach meant closing their doors forever. The impacts on small businesses is excentuated greatly....

Nov 9, 2019 | Applications, Best Practices, Business, China, Cyber breaches, cyberattacks, Cybercrime, Entertainment, Government, Hackers, Hacking, Hacking, Intellectual Property Theft, Internet, Malware, Nationstates, Patching, Radio Show, Radio_Show, safety, Security, Security, Security Alerts, Social Media, spying, Technology, TikTok, Updates
National Security and the Chinese-based Social App TikTok Have you or Do your kids use TikTok? TikTok is a wholely owned Chinese based video platform that is popular in social media circles. It boast a user base of a half-a-billion. What the government is...

Nov 9, 2019 | Applications, Applications, Audit Logs, Best Practices, Business, cyberattacks, Hacking, Hacking, Internet, Judicial, Legal, Liability, Patches, Patching, Radio Show, Radio_Show, Ransomware, Ransomware, Resources, Security, Security, Security Alerts, Software As A Service, Software Manufacturers, Technology, Third-Party, Updates
Lawfirm Software attacked by Ransomware Legal offices use case management software to assist them in preparing for trials. One of the largest providers is a company called TrialWorks. Unfortunately, a cybercriminal was able to launch a REvil/Sodinokibi...

Nov 9, 2019 | Applications, Applications, Artificial Intelligence, Audit Logs, audit logs, automation, Best Practices, bluetooth, Business, cameras, cyberattacks, Cybercrime, Cybersecurity, Encryption, gadgets, Hackers, Hacking, Hacking, Health, Hospital, Infosec, Internet, IoT, Liability, Malware, Mobile Phones, Patches, Patching, Privacy, privacy, Radio Show, Radio_Show, safety, Security, Security, Security, Security, Security Alerts, segmentation, Smart Home, Software, Technology, Third-Party, Updates, Updates
Cybercrime is Zeroing in on Healthcare Organizations It seems that almost everything today is connected and more connections to the internet are made daily. One industry where this is more problematic is Healthcare. Why? Medical data is worth big bucks — up to...

Nov 9, 2019 | Anti-Virus, Best Practices, Big Data, Breaches, Business, CEO, Consumer, Cyber Insurance, cyberattacks, Cybercrime, Data, Equifax, Hackers, Hacking, Hacking, Hacking, Liability, Patching, Radio Show, Radio_Show, Security, Security, Security Alerts, Technology, Updates
Equifax “Security” – Allowed Unbelievable Inept Logins and Lack of Encryption Most of us do not have a choice when it comes to sharing our data with big data credit bureaus/respositories. They simply take all our information and re-sell it making huge...








