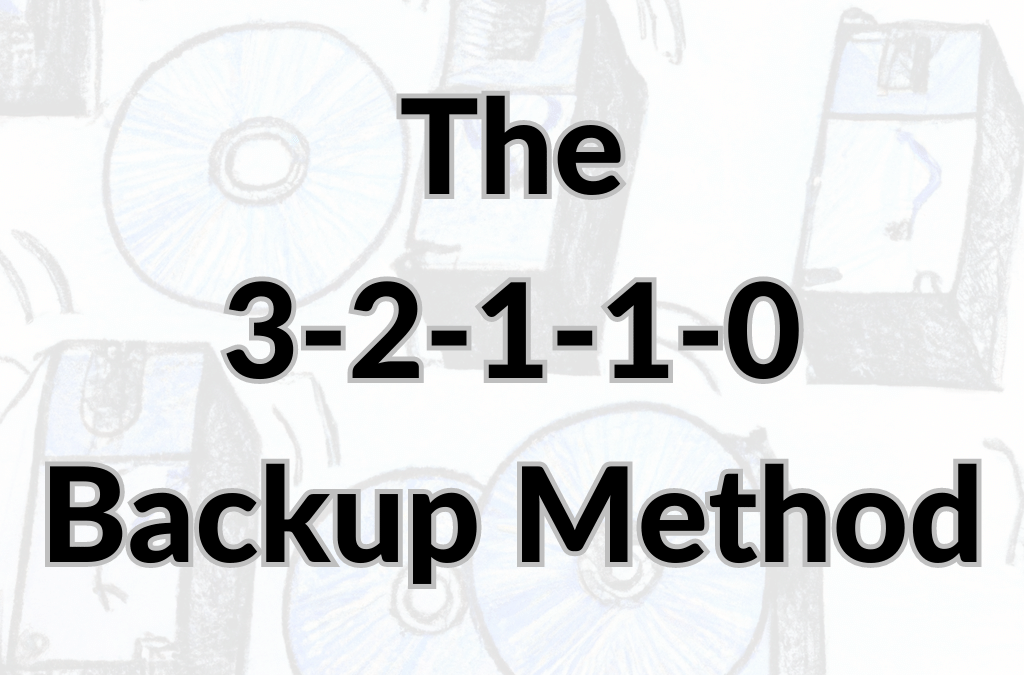
Mar 11, 2023 | Asset Management, Backup, Cyber breaches, Data Assets, Ransomware, Security
All businesses began as small businesses and are the lifeblood of our economy. With more than half of all jobs in the US provided by small companies, it is incredible that almost one-third never back up their data. Scary? No, it’s worse; those who did a backup...

Apr 27, 2020 | Asset Management, Backup, Business, Business Email Compromise, CEO, Compliance, Computers, Corporate Reputation, Cyber Liability, cyberattacks, Cybercrime, Cybersecurity, Cybersecurity Professional, Data Assets, Data Loss, Data Storage, Disaster Recovery, Employees, Employment, Employment, Executives, Firewalls, Hacking, Hard Disks, Hiring, Incident Response, Intellectual Property Theft, Intricate Data Systems, IT Professional, Laptops, Legacy Systems, Managed Security Services Provider (MSSP), Networking, Patching, Ransomware, Routers, Security, Security Alerts, Shadow-IT, Software As A Service, Technology, Technology, Third - Party, Updates, VPN
Overcoming the Critical Cybersecurity Talent Shortage Businesses are in Crisis mode, and it is going to get worse. Currently have more open cybersecurity jobs available than we have people to fill them, and these numbers will continue to expand in the years ahead. And...

Mar 21, 2020 | Backup, Business, Compliance, Computers, Corporate Reputation, credentials, Critical data, Cyber Liability, cyberattacks, Data Loss, Data Storage, Employees, Firewalls, Government, Intellectual Property Theft, Internet, Malware, Networking, News, Patching, Quarantine, Radio Show, Radio_Show, Remote-Work, Routers, Security, Security Alerts, Technology, Unsecured Devices, Updates, VPN
Your Employer Says Go Home and Work — Now what? For many companies and their employees, this widespread hysteria over this coronavirus pandemic has taken everyone by surprise. Remote work might have been a consideration but now is not an option but a...
Jan 18, 2020 | Anti-Virus, Applications, Applications, Attack Vectors, Audit Logs, Backup, Best Practices, browsers, Business, Business Email Compromise, Compliance, credential stealing, Cyber breaches, Cyber Liability, cyberattacks, Cybercrime, Cybersecurity, Data, Data Assets, Data Storage, Email, Employees, Employees, Fines and Penalties, Firefox, Government, Hackers, Hacking, Hacking, Hacking, Intellectual Property Theft, Internet, Legacy, Legacy Systems, Liability, Malware, Malware, Nationstates, Networking, Passwords, Patches, Patching, Phishing, Privacy, Radio Show, Radio_Show, Ransomware, Ransomware Attack, safety, Security, Security, Security Alerts, Signature-Based, Software, Technology, Third - Party, Updates, Updates, VPN, Vulnerabilities, Zero-Day
Updates, Patches and Hackers Oh My! Most data breaches ard due to hackers exploiting known vulnerabilities. I know, I hear it all the time – patching takes time, and it can indeed be risky, especially if you have any legacy hardware or software in your network...

Jan 11, 2020 | Access Controls, Amazon, Apple, Asset Management, Attack Vectors, audit logs, Backup, Big Tech, Business, Computers, Cyber breaches, Cybercrime, Cybersecurity, Data, Data Assets, data sharing, Data Storage, Employee Training, Employment, Encryption, Fines and Penalties, Google, Hacking, Incident Response, industrial espionage, Insider Threat, Internet, Jobs, Legal, Liability, Malware, Malware, Microsoft, Monitoring, Networking, predictive algorithms, Radio Show, Radio_Show, Ransomware, Security, Software As A Service, Surveillance, Technology, Zero-Day
How Mature is Your Insider Threat Intelligence? Are insiders a threat to your business? How would you know? Today it is necessary for companies to establish a robust insider threat program that can detect employee-created risk and respond accordingly but keeping...
Jan 11, 2020 | Applications, Artificial Intelligence, Asset Management, Attack Vectors, Audit Logs, audit logs, Backup, Business, CEO, Cloud, Cloud Provide, Cloud Vendors, Compliance, Computers, Cyber breaches, Cyber Insurance, Cyber Liability, cyberattacks, Cybercrime, Cybersecurity, Cybersecurity Professional, Data, Data Assets, data sharing, Data Storage, Databases, Employees, Fines and Penalties, Government, Hacking, Hacking, Incident Response, Incident Response, industrial espionage, Intellectual Property Theft, Internet, Machine Learning, Malware, Managed Security Services Provider (MSSP), Microsoft, Networking, Operating Systems, Patching, predictive algorithms, Radio Show, Radio_Show, Security, Security Alerts, Software As A Service, Technology, Third - Party, Updates, Vulnerabilities
Cloud Migration Considerations to Take into Account Deciding to move to business technology services to “the Cloud” is one of the most significant that is made by business leaders, and it is a decision best not made without the approval at the highest...






