Jan 18, 2020 | Anti-Virus, Applications, Applications, Attack Vectors, Audit Logs, Backup, Best Practices, browsers, Business, Business Email Compromise, Compliance, credential stealing, Cyber breaches, Cyber Liability, cyberattacks, Cybercrime, Cybersecurity, Data, Data Assets, Data Storage, Email, Employees, Employees, Fines and Penalties, Firefox, Government, Hackers, Hacking, Hacking, Hacking, Intellectual Property Theft, Internet, Legacy, Legacy Systems, Liability, Malware, Malware, Nationstates, Networking, Passwords, Patches, Patching, Phishing, Privacy, Radio Show, Radio_Show, Ransomware, Ransomware Attack, safety, Security, Security, Security Alerts, Signature-Based, Software, Technology, Third - Party, Updates, Updates, VPN, Vulnerabilities, Zero-Day
Updates, Patches and Hackers Oh My! Most data breaches ard due to hackers exploiting known vulnerabilities. I know, I hear it all the time – patching takes time, and it can indeed be risky, especially if you have any legacy hardware or software in your network...

Dec 19, 2019 | Applications, Audit Logs, Best Practices, Business, cell phones, credentials, Employees, Employees, Intellectual Property Theft, Internet, Malware, Mobile Phones, Patching, Radio Show, Radio_Show, Regulatory Compliance, safety, Security, Security, Security Alerts, spying, Technology, Updates
Business Computers Should Only Be Used For Business If an employer provides you with equipment, they expect that the computer to be used for work and work only. Many times there will be software installed on these devices that monitors your activities and...

Nov 16, 2019 | Best Practices, Business, Business Email Compromise, credential stealing, credentials, Cyber breaches, cyberattacks, Cybercrime, Cybersecurity, CyberTraining, Employees, Employees, Hackers, Hacking, Hacking, Hacking, Liability, Phishing, Phishing, Radio Show, Radio_Show, Security, Security, Technology, third-world
Can You Detect A Phishing Attempt? Cybercriminals are getting better at crafting believable and sophisticated ilephishing emails that are undetectable from legitimate emails. Do you know how to spot them? If you suspect that an email is not legitimate you can...
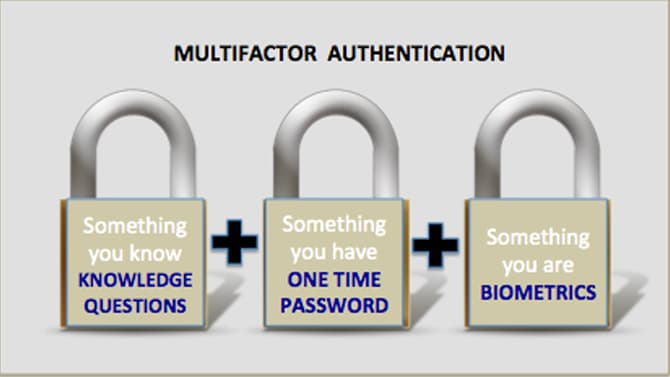
Nov 16, 2019 | 2FA, Best Practices, Business, Computers, credentials, Cyber breaches, cyberattacks, Cybersecurity, Employees, Employees, Hacking, Hacking, hardware token, Internet, Laptops, Malware, MFA, Phishing, Radio Show, Radio_Show, Security, Security, Technology
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...

Nov 9, 2019 | Best Practices, Business, Computer Repair, Contractors, Cybersecurity Professional, CyberTraining, Employees, Employees, Employment, Future Workforce, Internet, IT Professional, Psychology, Radio Show, Radio_Show, Security, Security, Stress, Technology
Job Dissatisfaction is prominent among IT Security Professionals Many Cybersecurity professionals love a challenge. They do not enjoy the doldrums of make work security. They long for excitement and challenging work. They are in demand so it is not suprising...

Nov 9, 2019 | Applications, Artificial Intelligence, Audit Logs, Best Practices, Business, credentials, Cyber breaches, cyberattacks, Cybercrime, CyberTraining, data sharing, Data Storage, Databases, Employees, Employees, Firewalls, Firewalls, Hackers, Hacking, Hacking, Hacks, Hard Disks, Intellectual Property Theft, Laptops, Liability, Malware, Malware, Networking, Networking, Patching, Radio Show, Radio_Show, Ransomware, Routers, Security, Security, Security Alerts, segmentation, Software As A Service, Switches, Technology, Updates
Cyberbreaches cause Small Businesses to Close Cybercriminals have found a lucrative new target – the small business. Unfortunately, for a tenth of them the breach meant closing their doors forever. The impacts on small businesses is excentuated greatly....






