Sep 21, 2019 | Algorithms, anonymity, Banking, Banking, Bitcoin, Cryptocurrency, Cryptocurrency, Cybercrime, Dark Web, data sharing, Featured, Financial, Malware, Marketplace, Open Source, Organized Crime, Radio Show, Radio_Show, Ransomware, Ransomware, Ransomware, scam, Security, Technology, Valuations
Warning About Security of Cryptocurrency If you have listened to me for a while, you know how I feel about Cryptocurrencies, and it looks like I was right all along. It is fraught with fraud that prays on peoples hopes and dreams. The criminal activity of ransomware...

Sep 21, 2019 | Android, Android, Business, Cell Phone, cell phones, Cellular Services, iOS, iPhone, Mobile, Mobile Phones, Passwords, Phone, Phones, Privacy, Radio Show, Radio_Show, scam, Security, Security Alerts, Smart Phone, T-Mobile, Technology
Major Cell Carrier Program Protects Customers from SimSwapping T-Mobile is taking action against the social engineering attack known as Sim Swapping. Using a non-advertised and rather private feature knowns as “NOPORT” to prevent the tricking of their...

Aug 17, 2019 | Best Practices, Business, Cybercrime, CyberTraining, Employees, Employees, Hackers, Hacking, Hacking, Liability, Malware, Malware, Passwords, Phishing, Privacy, Radio Show, Radio_Show, Ransomware, Regulatory Compliance, scam, Security, Security, Technology
Phishing — Best Practices One of the most persistent security challenges is phishing. This is true for both organizations and individuals. Whether gaining access to credit card information, security passwords, or any other sensitive information, hackers can use...

Aug 17, 2019 | Cybercrime, CyberTraining, Employees, Encryption, Financial, Hackers, Hacking, Internet, Malware, Passwords, Radio Show, Radio_Show, scam, Security, Security, Security, Social Networking, Technology
Technology Makes Crime Easier In part one of TechRepublic’s four-part series “Mastermind con-man behind Catch Me If You Can talks cybersecurity” TechRepublic’s Karen Roby sat down with Frank Abagnale, the famous con man turned FBI...
Aug 10, 2019 | Best Practices, Business, Cloud Vendors, Computers, Cryptocurrency, Cyber breaches, Cybercrime, Financial, Hackers, Hacking, Hacking, Internet, IoT, Liability, Malware, Nationstates, North Korea, Radio Show, Radio_Show, Ransomware, Ransomware, scam, Security, Security, Technology
North Korea. What do you think when you hear about this country? You probably think of a nation that has separated from progress and technology. A country run by a socialist despot. A hermit kingdom that strictly controls the daily activities of its people. A country...
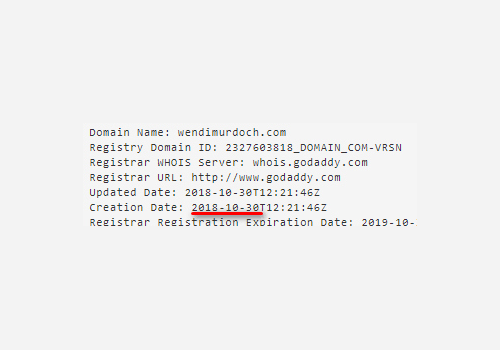
Jan 26, 2019 | Radio Show, scam
How A WhoIs Check Could Have Halted A Scam A Wendi Deng Murdoch imposter tricked photographers into paying for flights to and photography permits in Indonesia, and a more thorough Whois lookup could have saved the victims from losing money and time. CNN reports about...





