eMail encryption tools highly vulnerable

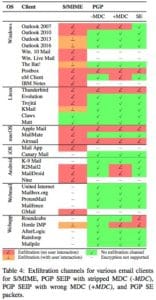
Major news in the security world as the email encryption standard used worldwide is shown to have a gaping hole. s/MIME, the protocol that was bolted onto the email protocol to provide security, actually allows attackers to see decrypted emails rather simply. Full details will be available Tuesday, May 15th.
Security researcher and professor Sebastian Schinzel has described the attack vector in tweets today. “There are currently no reliable fixes for the vulnerability. If you use PGP/GPG or S/MIME for very sensitive communication, you should disable it in your email client for now.”
The bottom-line recommendation from security researchers? Stop using PGP/GPG and email encryption until the problem is fixed.
The problem is readily fixable, and we can expect patches to come out from all of the major email software providers, including Apple and Microsoft. Until that time the recommendation is to disable email encryption and find other ways to communicate securely. More information is available from the EFF.
The GPGTools/GPGMail team has posted a temporary workaround against the vulnerability:
"Efail": as a temporary workaround against "efail" (https://efail.de ), disable "Load remote content in messages" in Mail → Preferences → Viewing. GPG Suite 2018.2 which mitigates against this attack is coming very soon.