The Latest in Tech Today
Best Practices in Authentication Still Mostly Ignored By Businesses
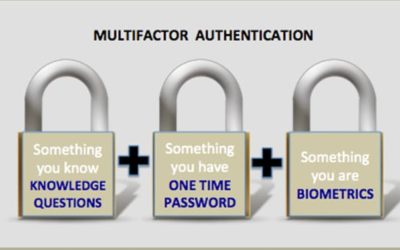
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...
Job Dissatisfaction is prominent among IT Security Professionals
Job Dissatisfaction is prominent among IT Security Professionals Many Cybersecurity professionals love a challenge. They do not enjoy the doldrums of make work security. They long for excitement and challenging work. They are in demand so it is not suprising...
Cyberbreaches cause Small Businesses to Close
Cyberbreaches cause Small Businesses to Close Cybercriminals have found a lucrative new target - the small business. Unfortunately, for a tenth of them the breach meant closing their doors forever. The impacts on small businesses is excentuated greatly. A...
National Security and the Chinese-based Social App TikTok
National Security and the Chinese-based Social App TikTok Have you or Do your kids use TikTok? TikTok is a wholely owned Chinese based video platform that is popular in social media circles. It boast a user base of a half-a-billion. What the government is...
Lawfirm Software attacked by Ransomware
Lawfirm Software attacked by Ransomware Legal offices use case management software to assist them in preparing for trials. One of the largest providers is a company called TrialWorks. Unfortunately, a cybercriminal was able to launch a REvil/Sodinokibi...
Online Voting is a Disaster waiting to Happen
Online Voting is a Disaster waiting to Happen If it is connected it can be hacked. The risk of only digital data that can not be audited is just a sure way to assure meddling and hacking of our elections. The integrity of our elections must remain paramount if...
Powerful Apps allow Control for…. Ever!
Powerful Apps allow Control for…. Ever! Many companies are creating apps and they are powerful. They are convenient and offer ease of use to their product lines. However, they may not have concidered the implications when not used in the manner that they...
Oops —- We Designed Technology to be Unpatchable
Oops —- We Designed Technology to be Unpatchable IoT or Internet of Things devices are becoming more and more popular. It seems that all types of items we never considered to require connectivity are now connected to the internet. They are constantly passing...
Technology idea that started 50 years ago but we rely on today
Technology idea that started 50 years ago but we rely on today It has taken 50 years to bring the network we know today as the internet to this point. In October 1969 the Advanced Research Projects Agency designed a network that research investigators could...
Cybercrime is Zeroing in on Healthcare Organizations
Cybercrime is Zeroing in on Healthcare Organizations It seems that almost everything today is connected and more connections to the internet are made daily. One industry where this is more problematic is Healthcare. Why? Medical data is worth big bucks — up to...
Equifax “Security” – Allowed Unbelievable Inept Logins and Lack of Encryption
Equifax “Security” - Allowed Unbelievable Inept Logins and Lack of Encryption Most of us do not have a choice when it comes to sharing our data with big data credit bureaus/respositories. They simply take all our information and re-sell it making huge profits...
Little Inexpensive Devices Can Remove Sensitive Data
Little Inexpensive Devices Can Remove Sensitive Data Who has access to your offices? I am sure you are familiar with those little USB drives that are almost flat, to be undetectable when installed. Well, these under $20 devices can be connected in computers...
Security 101 – Passwords and Password Management
Common Password Vulnerabilities and How to Avoid Them There are a couple of interesting articles this week discussing one of my favorite subjects because it can make a significant impact on your security stance. Breaches that could result in data loss are the...
Cyber Cold War Right on Our Door Step
Cyber Cold War Right on Our Door Step Nation-State sponsored cybercrime is on the upswing. China, as an example, has an entire cyber army that it dispatches to US university programs and US businesses as well as to third party providers world-wide who offer...
International News Hits the Dark Web
International News Hits the Dark Web Privacy is paramount, and it is one reason that the US government designed and implemented the TOR project. Now there is another reason, and that is preventing censorship of thought. That is the main reason that major...
When Businesses Are Required to Capitulate to Chinese Society
When Businesses Are Required to Capitulate to Chinese Society China is forcing companies to deliver content that is not culturally acceptable to Chinese society. Many companies and organizations are capitulating with these requirements to do business in China....
Cloud Players Vie for Pentagon Contract
Cloud Players Vie for Pentagon Contract The Pentagon wants to make their data more accessible to their divisions no matter the location and began looking for a trusted Cloud Provider. They put out a bid for their Joint Enterprise Defense Infrastructure (JEDI.)...
Privacy and China — Not So Much
Privacy and China -- Not So Much China is planning on developing its digital currency due to the rising costs of currency circulation and lack of control. China, a communist society, wants to control everything about its citizens. That goes on to include how, when,...
Are PaleBlue Batteries Your Next Battery?
Although they're still in Kickstarter, I managed to get my hands on some PaleBlue batteries. So far, so good. Pale Blue says that these batteries will save you some $3,000 But, they'll also save you a ton of hassles and time! They have built-in micro-USB ports you can...
Are your Apps Leaking? Unpatched Vulnerabilities Lead to Leaking Apps
Just because you download an app does not mean that it is not vulnerable to exploit or data leaks. The chance of it happening is even higher for those not in traditional app stores. Additionally, businesses depend on older software applications are at a great risk...
Walking through Virtual Reality to Work
Virtual Reality is coming to your walk to work. Titled “DreamWalker” researchers at Microsoft are developing some new VR prototype technologies that they say allows people to safely navigate through real-world environments while envisioning themselves strolling in a...
Plaintiffs in Facebook Class Action Awarded Standing
Plaintiffs in Facebook Class Action Awarded Standing Plaintiffs in a $35 billion class-action suit against Facebook won their argument proving standing to sue. This lawsuit concerns the collection and storage of millions of users' biometric data without...
Military Equipment — the Future is On our Door Step
Military Equipment -- the Future is On our Door StepAutonomous Military Vehicles are under development as part of the Army Futures Command Next-Generation Combat Vehicle program. Four companies have been selected to build non-developmental prototypes. The hope is...
Exploitable Vulnerability Allows Major VPN Breaches – NORDVPN and Others
Exploitable Vulnerability Allows Major VPN Breaches 3000 Servers hacked, the blame is being pointed at a third-party provider utilizing a remote management system in the data center. Who owned the data center? That would be NordVPN, a popular consumer VPN provider....
Chinese Using Visas to Import Corporate Spies and Thieves
Chinese Using Visas to Import Corporate Spys and Thieves It is about time that some of these Nation-State cyber hackers are going to prison for stealing intellectual property from our US Companies and government contractors. If you are not aware the Chinese...
They Look Cool But How Safe Are They?
They Look Cool but How Safe Are They?I have been warning about these embedded handles for a while. As you may know, I spent 10+ years as a volunteer advanced EMT where I responded to a number of accidents. Handles that completely fold inside the door are dangerous...
Is someone eavesdropping on your Smart Speaker?
Is someone eavesdropping on your Smart Speaker? Are your smart speakers listening to everything -- all the time. Somewhat. But It turns out that some third-party apps or those don’t natively belong to Google or Amazon may be piggybacking in and eavesdropping. ...
Watch This If You: Have Been Getting Unknown Calls or Texts; Noticed Your Phone is Getting Hot; Noticed Slowness on Your Smartphone; Need to Understand Social Engineering
Convenience Gadgets – Design, Functionality then Security
Convenience Gadgets - Design, Functionality then Security The first half of this year has been marked with a rampant increase on all those little gadget devices known by the acronym, IoT. These are any small device or controller that is network connected....
Facebook’s Libra cryptocurrency loses all but one payment company
Facebook’s Libra Cryptocurrency Loses all but One Payment Company Cryptocurrency is a fool's game. It is not ready for primetime and is not an investment. No matter how many get into it, the infrastructure to support this new currency change is not yet under...