The Latest in Tech Today
Thousands of Horses Escape — Now Microsoft is Starting to Close the Barn Door
Thousands of Horses Escape -- Now Microsoft is Starting to Close the Barn Door It might be difficult to fathom how this isn’t already mandatory, but Microsoft Corp. says it will soon force all Cloud Solution Providers (CSPs) that help companies manage...
Insecurity Strike Again – Major MSP Hack
Insecurity Strike Again - Major MSP Hack Hackers breached the infrastructure of PCM Inc., one of the major U.S.-based cloud solution provider. According to the popular investigator Brian Krebs, the attackers gained access to email and file sharing systems for...
Got Chinese Security Cameras? Just Try to Remove them.
Got Chinese Security Cameras? Just Try to Remove them. U.S. federal agencies have five weeks to rip out Chinese-made surveillance cameras in order to comply with a ban imposed by Congress last year in an effort to thwart the threat of spying from Beijing. But...
Worried About Privacy? Steve Wozniak says Delete Facebook
Worried About Privacy? Steve Wozniak says Delete Facebook Steve Wozniak is the latest high-profile naysayer to speak out against Facebook. The Apple co-founder, who deleted his own Facebook profile last year, told TMZ recently that he recommends most people...
Hollywood Could Hit the Skids with Virtual Stars
Hollywood on the Skids with Virtual Stars When you’re watching a modern blockbuster such as The Avengers, it’s hard to escape the feeling that what you’re seeing is almost entirely computer-generated imagery, from the effects to the sets to fantastical creatures. But...
Chinese Ministry of State Security Attacks Major Companies Internal Networks
Chinese Ministry of State Security Attacks Major Companies Internal NetworksHackers broke into the internal networks on major companies, such as HPE and IBM, and stole corporate data and trade secrets. Then the attackers used the stolen information to target into...
Did You Turn of Tracking? Guess What? Apps are Still Tracking You.
Did You Turn of Tracking? Guess What? Apps are Still Tracking You Android Q, the next version of Google's mobile OS, is set to fix Android's broken permission system. However, versions in use now give developers easy ways to get around user preferences for apps not...
Apple has a problem with Zoom and so should you
Apple has a problem with Zoom and so should you After all of the drama over Zoom’s use of a hidden web server on Macs, Apple itself has decided to step in, TechCrunch reports. It is issuing a silent update — meaning your Mac will get it without any interaction...
New MacBooks Coming
New MacBooks ComingThe “cheap” MacBook Pro—a 13-inch model starting at a mere $1,299—has been refreshed with an 8th-generation, 1.4GHz Intel Core i5 quad-core processor, a welcome upgrade from the 7th-generation, 2.3GHz Intel Core i5 dual-core chip the laptop...
Someone’s Phishing For You
Someone’s Phishing for You! Black Hats are out there casting a line for you and hoping to land their “Phish” This type of social engineering relies on a simple human trait - trust. By playing on this trust, they can manipulate you into falling for their plot...
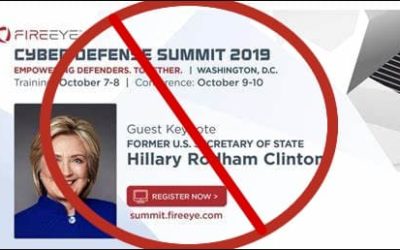
Hillary Clinton and CyberSecurity — In What Universe?
Hillary Clinton and CyberSecurity — In What Universe? Former Secretary of State Hillary Clinton withdrew from the cybersecurity conference where she was scheduled to be the keynote speaker, citing an “unforeseen circumstance,” according to an email from the...
What Did You Say? The Forever Recordings of Alexa
What Did You Say? The Forever Recordings of Alexa If you (like so many of us) hate listening to recordings of your own voice, you may be in for an unpleasant future, as Amazon has confirmed it hangs on to every conversation you've ever had with an Alexa-enabled...
The Landscape of Streaming TV is Changing be prepared to Pay More
The Landscape of Streaming TV is Changing be prepared to Pay More The most watched show on US Netflix, by a huge margin, is the US version of The Office. Even though the platform pumps out an absurd amount of original programming – 1,500 hours last year – it...
IoT Insecurity Its a Problem for Businesses and Consumers Alike
It's high time consumers stop using insecure IoT devices that aren’t implementing adequate safety and privacy measures – if they're going to use them at all. Security researcher Paul Marrapese disclosed several alarming flaws impacting 2 million IoT devices back in...
Didn’t Update Your Outlook — Watch Out For Iranians Hacks
Didn’t Update Your Outlook — Watch Out For Iranians Hacks An ongoing Iranian government-backed hacking campaign is now trying to exploit a Microsoft Outlook flaw from 2017. The US Cyber Command has issued an alert that hackers have been actively going after...
O365 Non-Security – again
O365 Non-Security - again The US Cybersecurity and Infrastructure Security Agency (CISA) has become the latest government body to plead with admins to implement security best practices on Microsoft's Office 365 platform. The UK's National Cyber Security Centre...
Crypto trust is costly and hidden
Crypto trust is costly and hidden The world’s first cryptocurrency ATM opened for business in a Canadian coffee shop on October 29, 2013, and by the end of the day, 81 people had visited the novel machine to trade their cash for bitcoin or vice versa. This...
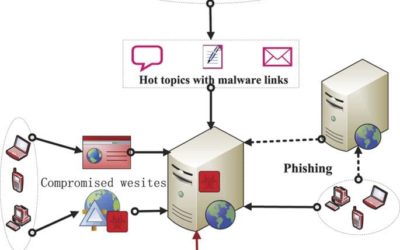
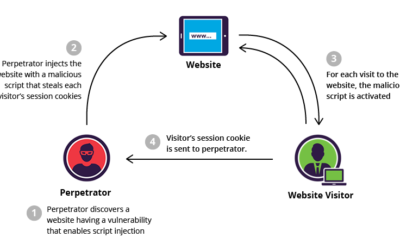
Organized crimes latest drive-by’s attacking website visitors
Organized crimes latest drive-by’s attacking website visitors An ongoing operation that’s installing ransomware and other malware on the computers of unsuspecting website visitors is one of the most potent drive-by attack campaigns researchers have seen in...
Be Careful What You Browse — Drive By Malware on the Rise
Be Careful What You Browse -- Drive-By Malware on the Rise An ongoing operation that’s installing ransomware and other malware on the computers of unsuspecting website visitors is one of the most potent drive-by attack campaigns researchers have seen in recent...
Are You Ready? Iranian Cyber Counter Attacks
Are You Ready? Iranian Cyber Counter Attacks U.S. businesses should get ready for a barrage of digital retaliation from Iran after the Trump administration launched a cyber attack against the Islamic Republic’s rocket and missile launching systems, current, and...
Cyberbreaches — How far does your liability extend?
Cyber Breaches -- How Far Does Your Liability Extend?It seems like we read about a major data breach occurring almost every other day. From credit card information and PIN codes stolen from some of the largest retailers in America to very personal health records, data...
What We Know About Apollo Missions After 50 years
What We Know About Apollo Missions After 50 years50 years ago, on July 20, 1969, humanity took our first footsteps on the surface of another world. With Neil Armstrong's small step for a single man, humankind took a great leap forward into the space age, demonstrating...
Trumping Iranian Aggression
Trumping Iranian Aggression The US has responded to a recent rise in Iranian cyber-activity and the shooting of an unarmed drone last week by launching cyber-attacks against Iran's military IT systems. The cyber-attacks were carried out by US Cyber Command with...
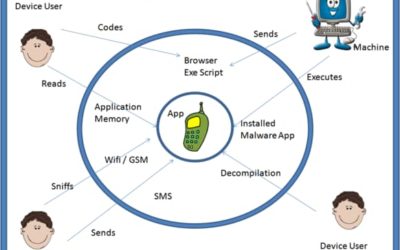
Is Your App Safe? Maybe Not!
Is That App On Your SmartPhone Safe? Maybe Not! High-risk vulnerabilities are common across both Android and iOS mobile apps, with Android devices slightly more at risk than their iOS counterparts (43% vs. 38%), according to Positive Technologies'...
We Will Need 3.5 Million Cybersecurity Professionals by 2021 and They Won’t Come Out Of Our Colleges
We Will Need 3.5 Million Cybersecurity Professionals by 2021 and They Won't Come Out Of Our Colleges Unfilled cybersecurity jobs are expected to reach 1.8 million by 2022, up 20% from 1.5 million in 2015, according to the Center for Cyber Safety and Education....
Mac Non-Vulnerability Vulnerability
Mac Non-Vulnerability Vulnerability Mac malware developers have jumped on a recently disclosed macOS Gatekeeper vulnerability and are actively developing malware that abuses it. The new malware has been named OSX/Linker and has been tied to the same group that...
During Travel Is Your Data Safe from Snooping Eyes?
During Travel Is Your Data Safe from Snooping Eyes? Visual hacking—when someone can see information on your screen over your shoulder without your knowledge—is a major cybersecurity threat to business travelers, especially in the GDPR era, according to a Monday...
Who Is Your Biggest Cyber Liability? Maybe It Is Not Who You Think
Who Is Your Biggest Cyber Liability? Maybe It Is Not Who You Think. If a poll were taken and the top threats to our national and cybersecurity were voted on, the usual suspects would be easy to name: China, Russia, North Korea, and Iran. You’d be half right....
Who has the Moral High Road Google Search or News Media
Who has the Moral High Road Google Search or News Media Are publishers losing money because of Google and Google's news service? Or are they becoming more profitable? This week, The New York Times accused Google of this. It boils down to an industry report that...
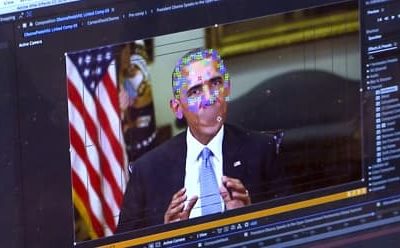
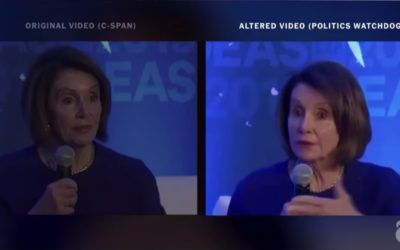
Deep Fakes Are No Laughing Matter
Deep Fakes Are No Laughing MatterIn a video published on YouTube, Game of Thrones actor Kit Harington—in character as Jon Snow—apologized for several mistakes made during the controversial eighth season of the hit HBO show. There’s just one problem: Harington never...