
Nov 30, 2019 | Business, Computers, Cyber breaches, cyberattacks, Cybercrime, Data Storage, Employees, Firewalls, Hackers, Hacking, Hacking, Hacking, Insider Threat, Intellectual Property Theft, Internet, Malware, Malware, Networking, Networking, Patching, Privacy, Radio Show, Radio_Show, Routers, Security, Security Alerts, segmentation, Technology, Updates, Vulnerabilities
Why Zero Trust Is the Answer to Internet Everywhere Connections Everyone everywhere has a mobile device, and connections to the internet are available whenever we want it. In our connected world, it means that keeping your businesses secure means fighting a...

Nov 30, 2019 | Anti-Virus, Best Practices, Big Tech, Business, Consumer, credentials, Cyber breaches, Cybercrime, Employees, Employment, Hackers, Hacking, Identity Theft, Insider Threat, Radio Show, Radio_Show, Security, Security, Technology, Vulnerabilities
Cybercriminals return to old-school ID theft tactics As security professionals come up with new protocols and software to protect companies and businesses implement them, hackers are finding themselves thwarted. So many of these cybercriminals are going...

Nov 23, 2019 | Blogging, Business, Consumer, Employees, Employment, Facebook, Google, Hacking, Identity Theft, Imposter Sites, Internet, LinkedIn, Radio Show, Radio_Show, Security, Technology
Hiring and Issues with Scam Online Applications With the economy buzzing along and employment at a full time high — finding workers for seasonal part time employment is getting harder and harder. However, these employers are now having to compete with...

Nov 16, 2019 | Business, Business Email Compromise, CEO, Consumer, credentials, Cyber breaches, Cybercrime, Cybersecurity, DeepFake, Employees, Employment, Exploits, Family, Hackers, Hacking, Hacking, HR, Liability, Phishing, Phishing, Psychology, Radio Show, Radio_Show, Security, Technology
Don’t Take The Bait – Fake Sexual Harassment Claims Scammers are phishing employees of large corporations using fake US EEOC sexual harrassment complaints to offload trojan payloads of Trickbot malware onto corporate computers which direct them to hand over...

Nov 16, 2019 | Best Practices, Business, Business Email Compromise, credential stealing, credentials, Cyber breaches, cyberattacks, Cybercrime, Cybersecurity, CyberTraining, Employees, Employees, Hackers, Hacking, Hacking, Hacking, Liability, Phishing, Phishing, Radio Show, Radio_Show, Security, Security, Technology, third-world
Can You Detect A Phishing Attempt? Cybercriminals are getting better at crafting believable and sophisticated ilephishing emails that are undetectable from legitimate emails. Do you know how to spot them? If you suspect that an email is not legitimate you can...
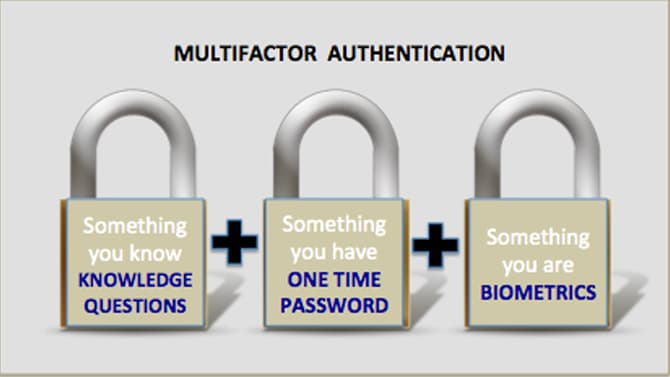
Nov 16, 2019 | 2FA, Best Practices, Business, Computers, credentials, Cyber breaches, cyberattacks, Cybersecurity, Employees, Employees, Hacking, Hacking, hardware token, Internet, Laptops, Malware, MFA, Phishing, Radio Show, Radio_Show, Security, Security, Technology
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...








