
Apr 30, 2021 | Apple, Automation, Automotive, Best Practices, Big Tech, Business, Cloud, Cloud, Cloud Vendors, CPU, Critical data, Cybercrime, Data, Databases, Emotet, FCC, Government, Hackers, Hacking, iMac, Internet, Laptops, Law Enforcement, Mac Pro, MacBook, Monitoring, News, Podcast, Police, Proprietary Design, Radio Show, Radio_Show, Ransomware, Ransomware, Security, Security, Security Alerts, Show Notes, Skyrocketing Ransoms, SpaceX, Starlink, Technology, Unsecured
Read. Learn. Share. Tech Talk Show Notes May 1, 2021 Lyft is getting out of the self-driving business Lyft has sold its self-driving division to a Toyota subsidiary called Woven Planet for $550 million—the latest sign that it takes deep pockets to compete in the...

Apr 27, 2020 | Asset Management, Backup, Business, Business Email Compromise, CEO, Compliance, Computers, Corporate Reputation, Cyber Liability, cyberattacks, Cybercrime, Cybersecurity, Cybersecurity Professional, Data Assets, Data Loss, Data Storage, Disaster Recovery, Employees, Employment, Employment, Executives, Firewalls, Hacking, Hard Disks, Hiring, Incident Response, Intellectual Property Theft, Intricate Data Systems, IT Professional, Laptops, Legacy Systems, Managed Security Services Provider (MSSP), Networking, Patching, Ransomware, Routers, Security, Security Alerts, Shadow-IT, Software As A Service, Technology, Technology, Third - Party, Updates, VPN
Overcoming the Critical Cybersecurity Talent Shortage Businesses are in Crisis mode, and it is going to get worse. Currently have more open cybersecurity jobs available than we have people to fill them, and these numbers will continue to expand in the years ahead. And...

Mar 21, 2020 | Agencies, Announcements, Best Practices, Biological Viruses, Biological Warfare, Business, Cable Companies, Cisco, Cloud, Cloud Vendors, Compliance, Computers, Coronavirus, Covid-19, Covid-19, Critical data, Cyber Liability, Data Storage, Domain Name Service, duck duck go, Employees, Encryption, Executives, FDA, Filtering, Firewalls, Firewalls, Government, Information Technology, Internet, IoT, Laptops, Malware, Networking, Networking, Operating Systems, Pandemic, Patches, Patching, Quarantine, Quarantine, Quarantine, Radio Show, Radio_Show, Regulatory Compliance, Remote Work, Remote-Work, Routers, Routers, Security, Security, Security Alerts, segmentation, Social Distancing, Software As A Service, Switches, Technology, Updates, Updates, VPN, VPN, WebEx, WHO
Being Successful While Remote Working If you’re starting to work from home or just got a remote position, you’re probably looking forward to not spending time on a frustrating commute and staying in your pajamas until noon. Enjoy that for the first day or two! But if...

Feb 29, 2020 | Apple, Apple, Attack Vectors, Best Practices, Big Tech, Cybercrime, Cybersecurity, Hackers, Hacking, iMac, iPad, Laptops, Mac Pro, MacBook, Malware, Patching, Radio Show, Radio_Show, Security, Security, Security Alerts, Security First, Tablet, Technology, Updates
Malware on Macs: Not as Bad as the Headlines Might Lead You to Believe Apple designs their computers with a security-first mindset but that does not mean that they are not able to be compromised by enterprising cybercriminals. Although, just like with all news...
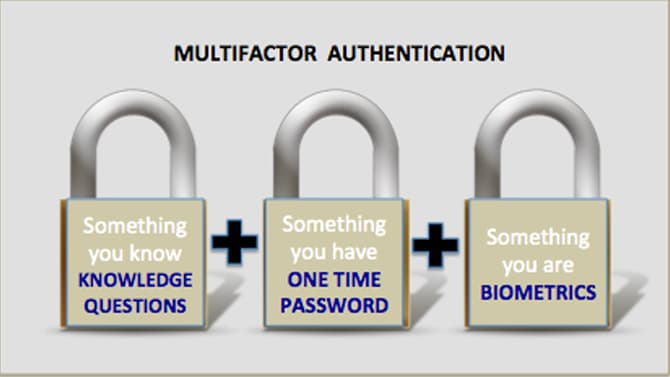
Nov 16, 2019 | 2FA, Best Practices, Business, Computers, credentials, Cyber breaches, cyberattacks, Cybersecurity, Employees, Employees, Hacking, Hacking, hardware token, Internet, Laptops, Malware, MFA, Phishing, Radio Show, Radio_Show, Security, Security, Technology
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...

Nov 9, 2019 | Applications, Artificial Intelligence, Audit Logs, Best Practices, Business, credentials, Cyber breaches, cyberattacks, Cybercrime, CyberTraining, data sharing, Data Storage, Databases, Employees, Employees, Firewalls, Firewalls, Hackers, Hacking, Hacking, Hacks, Hard Disks, Intellectual Property Theft, Laptops, Liability, Malware, Malware, Networking, Networking, Patching, Radio Show, Radio_Show, Ransomware, Routers, Security, Security, Security Alerts, segmentation, Software As A Service, Switches, Technology, Updates
Cyberbreaches cause Small Businesses to Close Cybercriminals have found a lucrative new target – the small business. Unfortunately, for a tenth of them the breach meant closing their doors forever. The impacts on small businesses is excentuated greatly....








