
Nov 30, 2019 | Best Practices, Business, China, Cyber breaches, Cybersecurity, Data, Economic Disruption, Hacking, Internet, Iran, Nationstates, North Korea, password spraying, Phishing, Phishing, Phishing, Privacy, Radio Show, Radio_Show, Russia, Security, Security, Security, Software, Technology, Vulnerabilities
Nation-State Cybecriminals and Economic Disruption Nation-state cybercriminals from Russia, China, North Korea, and Iran are attacking all parts of US society. They are attacking anything and everything that will disrupt our economy. They will attack our...

Nov 16, 2019 | Business, Business Email Compromise, CEO, Consumer, credentials, Cyber breaches, Cybercrime, Cybersecurity, DeepFake, Employees, Employment, Exploits, Family, Hackers, Hacking, Hacking, HR, Liability, Phishing, Phishing, Psychology, Radio Show, Radio_Show, Security, Technology
Don’t Take The Bait – Fake Sexual Harassment Claims Scammers are phishing employees of large corporations using fake US EEOC sexual harrassment complaints to offload trojan payloads of Trickbot malware onto corporate computers which direct them to hand over...

Nov 16, 2019 | Best Practices, Business, Business Email Compromise, credential stealing, credentials, Cyber breaches, cyberattacks, Cybercrime, Cybersecurity, CyberTraining, Employees, Employees, Hackers, Hacking, Hacking, Hacking, Liability, Phishing, Phishing, Radio Show, Radio_Show, Security, Security, Technology, third-world
Can You Detect A Phishing Attempt? Cybercriminals are getting better at crafting believable and sophisticated ilephishing emails that are undetectable from legitimate emails. Do you know how to spot them? If you suspect that an email is not legitimate you can...
Nov 16, 2019 | Business, Business Email Compromise, credential stealing, cyberattacks, Cybercrime, Cybersecurity, Email, Hackers, Hacking, Hacking, Identity Theft, Organized Crime, Phishing, Phishing, Radio Show, Radio_Show, Security, third-world
Bots Losing Panache as Cybercriminals Hire In Third World As our detection methods and tools improve, cybercriminals are changing tactics by employing workers from third world countries to steal credentials and money through phishing. It seems we are seeing a...
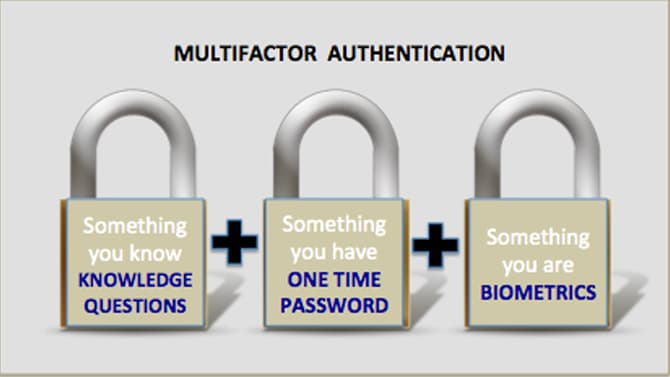
Nov 16, 2019 | 2FA, Best Practices, Business, Computers, credentials, Cyber breaches, cyberattacks, Cybersecurity, Employees, Employees, Hacking, Hacking, hardware token, Internet, Laptops, Malware, MFA, Phishing, Radio Show, Radio_Show, Security, Security, Technology
Best Practices in Authentication Still Mostly Ignored By Businesses How do cybercriminals breach into corporate systems? They use many tactics but on of the easiest is through the use of compromised credentials. The problems is that these are real valid credentials...

Sep 27, 2019 | Business, Business Email Compromise, Cell Phone, cell phones, CEO, Cyber breaches, Cybercrime, Email, Employees, Hackers, Hacking, Hacking, iPad, iPhone, Malware, Phishing, Radio Show, Radio_Show, Security, Smart Phone, Tablet
Spearphishing Mobile Devices of Executives Many businesses today use mobile technology as a primary executive communication channel. However, what happens if these devices are lost or stolen. That often is when they find the executives becoming targets of...







