The Latest in Tech Today
Intel No More: Apple Designs its Own Processors
Intel No More: Apple Designs its Own ProcessorsCovid-19 spells the end for Intel (at least for Apple). Next year Apple will be using its own proprietary CPU's an GPU's in its products. They will be basing the design of these on their company developed chip in use in...
Medical IoT Prone to Security Challenges
Medical IoT Prone to Security ChallengesHospitals are busy places, and anytime they can save time or make something more natural, they try to do so. Medical device companies are adding applications and creating real products to solve medical issues. Medical IoT...
The Apple Exploit that Wasn’t
The Apple Exploit that Wasn’t“This is a catastrophe,” my wife said—slightly horrified—as she swiped through page after page of apps on my phone. “Why do you even have most of these?” It’s a good question. It’s hard to believe that just a decade ago, the App Store icon...
Amazon’s Own Products designed by Data from Third-Party Sellers
Amazon’s Own Products designed by Data from Third-Party SellersIs Amazon playing fair with its third-party resellers? Or have they been using them to gather statistics and ideas to create popular products of their own? Amazon is a retail behemoth, but did they get...
Who Is Falling for COVID-19 Scams…Lots of People
Who Is Falling for COVID-19 Scams...Lots of PeopleHackers are spreading their scams widely in the face of the COVID-19 pandemic, and unfortunately, tricking many people into clicking on these fraudulent spam offers. Having been sequestered in our homes and feel the...
Malicious Insiders Monetize Their Knowlege Using Dark Web
Malicious Insiders Monetize Their Knowlege Using Dark WebHave you considered that you may have those inside your business who would do you harm? Cybercrime is no longer for hackers. The dark web has provided an outlet for information supplied by insiders to raise...
Collaboration Platforms Using AI to Help Remote Workers
Collaboration Platforms Using AI to Help Remote Workers With hundreds of thousands to millions of employees working from home during this pandemic, businesses are seeking ways to collaborate more manageable and with better efficiency. There are several platforms, some...
Cryptojacking
CryptojackingHi. Craig Peterson here with a blink into Cryptojacking. Has your Android phone been getting hot? I mean really hot. Has the battery life on your smartphone all of a sudden dropped to almost nothing? How about your desktop or laptop web browser. Is...
Pawned Accounts
Pawned AccountsHi. Craig Peterson here with a blink into the stolen account business, also known as “Pwning.” [Prounced “poned” as in p-owned] Pwned means that your account has been the victim of a data breach. Your username and password have been stolen from a...
Multi-factor Authentication
Multi-factor AuthenticationHi. Craig Peterson here with a blink into multi-factor authentication. Two-factor authentication, also known as multi-factor authentication, provides some of the highest levels of security available — Something you know along with...
VPNs and Security
VPNs and SecurityHi. Craig Peterson here with a blink into the dangers and benefits of VPNs. VPNs originally were to connect business networks together over the Internet, saving thousands of dollars per month over leased lines. Today, we’re using VPNs to watch...
Accidental risks in the home and on the road
Accidental risks in the home and on the roadHi. Craig Peterson here with a blink into accidental risks in the home and on the road. Some of the things we may not be thinking about when we’re working at home, or out of the office. There’s the physical dangers: ...
Recognizing and Avoiding Spyware
Recognizing and Avoiding SpywareHi. Craig Peterson here with a blink into spyware. To start with, the term "spyware" doesn't refer to the Russians. It isn’t the KGB. Spyware is also known as "adware."More specifically, it refers to software that, when installed on...
Keeping Security Up-To-Date
Keeping Security Up-to-DateHi. Craig Peterson here with a blink into upgrades, updates, and patches. Do you know which ones to pay attention to? I’m sure you’ve heard about the Equifax breach. The records of 140 million Americans, along with some British and...
Understanding Small Business Firewalls
Understanding Small Business FirewallsHi. Craig Peterson here. Hackers are more active today than they ever have been, so we’re going to take a quick blink at Understanding Firewalls for your Small Business or Home. When your computer is accessible through an...
USB Security
USB SecurityHi. Craig Peterson here with a blink into USB thumb drives. Some of the characteristics of those thumb drives we all use create real security problems: They’re easy to lose, and often contain private information. If you have encrypted your USB flash...
Securing Wi-Fi
Securing Wi-FiHi. Craig Peterson here with a blink into using Wifi. Our online lives revolve around Wifi. At home, at the office, and on the road. We’ve had Wifi for years, and yet we often don’t configure or use it correctly. In our homes and businesses, we...
Secure Use of Computers in Public
Secure Use of Computers in PublicHi. Craig Peterson here with a blink into using computers in public. Most people have their own computers nowadays, but we are using them more-and-more in public. We are plugging our devices into random USB ports to charge them. We...
Using Webmail Securely
Using Webmail SecurelyHi. Craig Peterson here with a blink into using webmail securely. The first free Webmail email services started in 1996. Remember Hotmail and Rocketmail? My friend Gary still uses Hotmail. Today, the most popular Webmail service is gmail,...
Why and When? Upgrades, Updates and Patches
Why and When? Upgrades, Updates and PatchesHi. Craig Peterson here with a blink into understanding Upgrades, Updates, and Patches. When/How/Why’s When vendors become aware of vulnerabilities in their products, they often issue patches to fix those vulnerabilities....
Generate strong passwords/passphrases
Generate strong passwords/passphrasesHi. Craig Peterson here with a blink into secure passwords. Many businesses insist that their eight character passwords are secure because they force complexity requirements, and frequent password updates. Not true. These...
Your mobile device is safer on the road/at home if you do a few things
You’re mobile device is safer on the road/at home if you do a few thingsHi. Craig Peterson here with a blink into mobile device security. The true cost of a lost mobile device goes far beyond the cost of replacement. Totaling up the expense of lost productivity,...
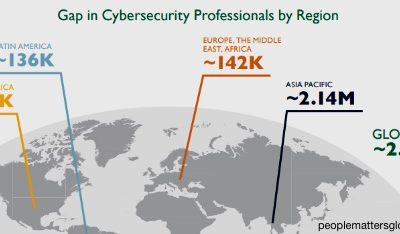
Overcoming the Critical Cybersecurity Talent Shortage
Overcoming the Critical Cybersecurity Talent ShortageBusinesses are in Crisis mode, and it is going to get worse. Currently have more open cybersecurity jobs available than we have people to fill them, and these numbers will continue to expand in the years ahead. And...
Thank you Coronavirus – Governments Are Watching Us
Thank you Coronavirus - Governments Are Watching Us Quarntines are meant to help control those who are capable of infection from interacting with the general populace. It is not meant to curtail all economic activity of the society. With this pandemic, governments...
Contact Tracing = Limited Privacy
Contract Tracing = Limited Privacy Inital projected models for the spread of this novel virus were designed specifically to ramp up fear. Big Tech and Governments are working on ways to try to control the spread of a pandemic that frankly is really not much worse than...
Conspiracy Theorists Grasping at 5G
Conspiracy Theorists Grasping at 5G There are always those who will believe the most phenomenal theories when they someone with scientific authority says comments on it. That is the case with the conspiracy theory that the radiation from 5G cell towers creates...
Pandemic Customers Buy but Amazon Can’t Deliver
Pandemic Customers Buy but Amazon Can’t DeliverWith our shopping abilities deeply curtailed by this forced government self-isolation to prevent the spread of COVID-19, we have turned to those who can supply our needs through online shopping. Turns out that for many...
Hijacked Routers – Securing Them Requires Password Reset
Hijacked Routers - Securing Them Requires Password ResetHackers have found a way to hijack user accounts and change the user settings on Linksys routers that use Smart WiFi accounts. When this is done users are now redirected them to malware sites. The Smart WiFi...
Your Zoom Account is Worth One ‘Copper’ to Hackers
Your Zoom Account is Worth One ‘Copper’ to Hackers Zoom has gained popularity during this pandemic’s require shelter in their homes. However its widespread use has unveiled to many the privacy and security issues inherent in this platform. These inherent...
Can America Compete? US iPhone vs Chinese iPhone
Can America Compete? US iPhone vs Chinese iPhone We should be manufacturing the products we use in America. American companies can compete with China and it actually would not be that much more expensive. For years we have heard about the Global supply chain but when...